Secure Microsoft BitLocker operation requires user authentication during the pre-boot-phase, typically referred as pre-boot-authentication – PBA. Microsoft offers a very limited set of secure pre-boot-authentication methods including TPM+Pin, password authentication, and a cryptographic key stored in clear-text on a USB-stick (the startup key). But what if a user can not logon and require helpdesk support?
In case a user forgets his TPM-Pin, or BitLocker password or loses the USB-stick with the startup-key a BitLocker recovery is required. In enterprises the domain admin need to hand over the 48-hex-digit BitLocker recovery key to the user to unlock the client to allow to reset TPM-Pin or BitLocker password.
The BitLocker recovery key is a obviously dangerous master key for the client and allow unlimited access to the encrypted client. Therefore, the recovery key need to be changed immediatelly after emergency usage through the user. In case an active BitLocker recovery key is lost along with the client, this incident need to be treated as a data breach.
Prevent Data Breaches with Intelligent BitLocker Helpdesk Methods
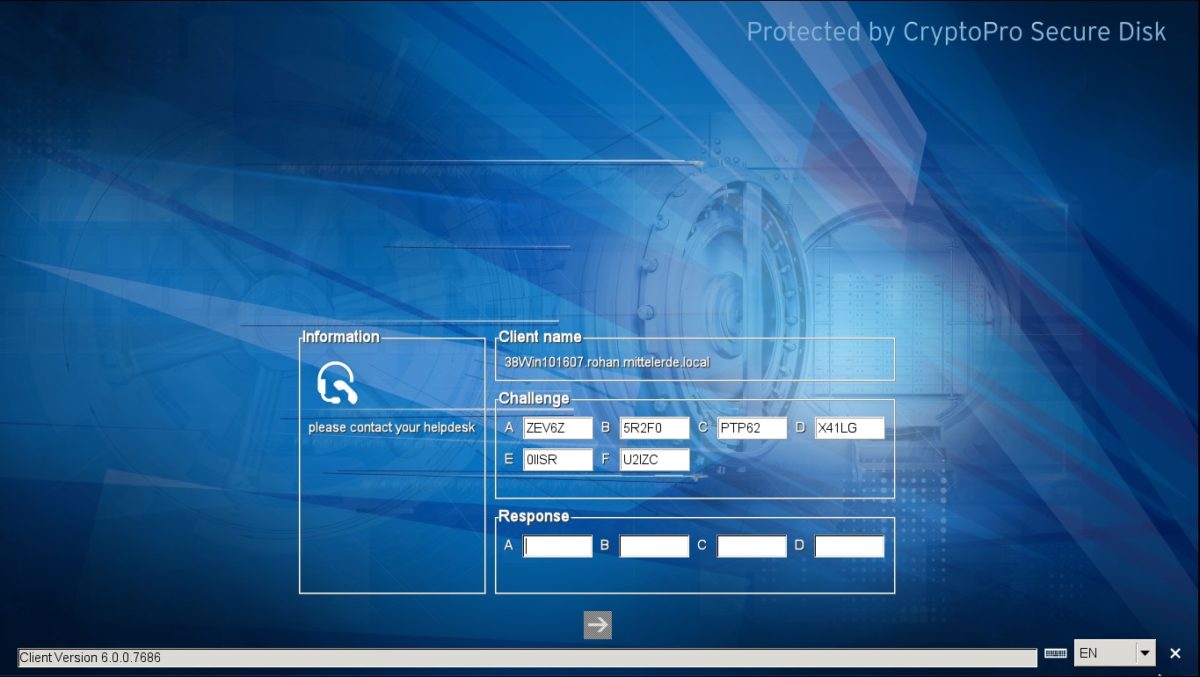
As the BitLocker recovery key is hard to handle and very sensitive if ever lost, Secure Disk for BitLocker offers a user convenient challenge/response helpdesk method without the limitations of the BitLocker recovery key.
The Secure Disk for BitLocker response can freely be defined to allow a new password to be set, a new smart card to be learned, temporary booted with out authentication for a number of boots or a defined time. Even the Windows domain password can be bypassed in case the users Active Directory password is lost.
Request our helpdesk console manual for a full list of Secure Disk for BitLocker helpdesk options.